
This is my blog, which I will be updating fairly regulary. Please remember to take everything I say with a pinch of salt, it’s really just my opinion on things.
- WordPress Space Cleanup: A Free WordPress Database and Media Library Cleanup Plugin
 If you run a WordPress site for any length of time, the database quietly fills with junk. Post revisions stack up every time you hit Save. Drafts you abandoned years ago sit there. Spam comments accumulate. Transients expire but never get deleted. Orphaned metadata from plugins you uninstalled months ago … Continue reading “WordPress Space Cleanup: A Free WordPress Database and Media Library Cleanup Plugin”
If you run a WordPress site for any length of time, the database quietly fills with junk. Post revisions stack up every time you hit Save. Drafts you abandoned years ago sit there. Spam comments accumulate. Transients expire but never get deleted. Orphaned metadata from plugins you uninstalled months ago … Continue reading “WordPress Space Cleanup: A Free WordPress Database and Media Library Cleanup Plugin” - What is Minification and How to Test if it is Actually Working
 1. What is Minification Minification is the process of removing everything from source code that a browser does not need to execute it. This includes whitespace, line breaks, comments, and long variable names. The resulting file is functionally identical to the original but significantly smaller. A CSS file written for … Continue reading “What is Minification and How to Test if it is Actually Working”
1. What is Minification Minification is the process of removing everything from source code that a browser does not need to execute it. This includes whitespace, line breaks, comments, and long variable names. The resulting file is functionally identical to the original but significantly smaller. A CSS file written for … Continue reading “What is Minification and How to Test if it is Actually Working” - Stop Selling Hampers: Why Enterprise Software Tiering Is a Self-Defeating Strategy
 By Andrew Baker, CIO at Capitec Bank There is a category of enterprise technology vendor whose approach to pricing is so fundamentally at odds with how purchasing decisions actually get made that it borders on self-defeating. Their commercial model is built on access gates, bundled tiers, and a deeply held … Continue reading “Stop Selling Hampers: Why Enterprise Software Tiering Is a Self-Defeating Strategy”
By Andrew Baker, CIO at Capitec Bank There is a category of enterprise technology vendor whose approach to pricing is so fundamentally at odds with how purchasing decisions actually get made that it borders on self-defeating. Their commercial model is built on access gates, bundled tiers, and a deeply held … Continue reading “Stop Selling Hampers: Why Enterprise Software Tiering Is a Self-Defeating Strategy” - WordPress Totally Free Backup and Restore: CloudScale Backup Plugin – Does Exactly What It Says
 I’ve been running this blog on WordPress for years, and the backup situation has always quietly bothered me. The popular backup plugins either charge a monthly fee, cap you on storage, phone home to an external service, or do all three. I wanted something simple: a plugin that makes a … Continue reading “WordPress Totally Free Backup and Restore: CloudScale Backup Plugin – Does Exactly What It Says”
I’ve been running this blog on WordPress for years, and the backup situation has always quietly bothered me. The popular backup plugins either charge a monthly fee, cap you on storage, phone home to an external service, or do all three. I wanted something simple: a plugin that makes a … Continue reading “WordPress Totally Free Backup and Restore: CloudScale Backup Plugin – Does Exactly What It Says” - Eliminating Render-Blocking JavaScript: The Easiest Core Web Vitals Win You’re Not Taking
 If you’ve run your site through Google PageSpeed Insights and seen the “Eliminate render-blocking resources” warning, you’ve probably wondered why something that sounds so simple is so hard to actually fix. The answer is that WordPress makes it surprisingly easy to load JavaScript the wrong way — and surprisingly difficult … Continue reading “Eliminating Render-Blocking JavaScript: The Easiest Core Web Vitals Win You’re Not Taking”
If you’ve run your site through Google PageSpeed Insights and seen the “Eliminate render-blocking resources” warning, you’ve probably wondered why something that sounds so simple is so hard to actually fix. The answer is that WordPress makes it surprisingly easy to load JavaScript the wrong way — and surprisingly difficult … Continue reading “Eliminating Render-Blocking JavaScript: The Easiest Core Web Vitals Win You’re Not Taking” - The Quantum Threat: Why the Encryption Protecting Your Data Today Won’t Survive Tomorrow
 Published on andrewbaker.ninja | Enterprise Architecture & Banking Technology There is a quiet revolution happening in physics laboratories around the world, and most of the people who should be worried about it are not paying attention yet. That is about to change. Quantum computing is advancing faster than anyone predicted … Continue reading “The Quantum Threat: Why the Encryption Protecting Your Data Today Won’t Survive Tomorrow”
Published on andrewbaker.ninja | Enterprise Architecture & Banking Technology There is a quiet revolution happening in physics laboratories around the world, and most of the people who should be worried about it are not paying attention yet. That is about to change. Quantum computing is advancing faster than anyone predicted … Continue reading “The Quantum Threat: Why the Encryption Protecting Your Data Today Won’t Survive Tomorrow” - Core Banking Is a Terrible Idea. It Always Was.
 The COBOL apocalypse conversation this week has been useful, because it has forced the industry to confront something it has been avoiding for decades. But most of the coverage is stopping at the wrong point. Everyone is talking about COBOL. Nobody is talking about the architectural philosophy that COBOL gave … Continue reading “Core Banking Is a Terrible Idea. It Always Was.”
The COBOL apocalypse conversation this week has been useful, because it has forced the industry to confront something it has been avoiding for decades. But most of the coverage is stopping at the wrong point. Everyone is talking about COBOL. Nobody is talking about the architectural philosophy that COBOL gave … Continue reading “Core Banking Is a Terrible Idea. It Always Was.” - CloudScale SEO AI Optimiser: Enterprise Grade WordPress SEO, Completely Free
 Written by Andrew Baker | February 2026 I spent years working across major financial institutions watching vendors charge eye-watering licence fees for tools that were, frankly, not that impressive. That instinct never left me. So when I wanted serious SEO for my personal tech blog, I built my own WordPress … Continue reading “CloudScale SEO AI Optimiser: Enterprise Grade WordPress SEO, Completely Free”
Written by Andrew Baker | February 2026 I spent years working across major financial institutions watching vendors charge eye-watering licence fees for tools that were, frankly, not that impressive. That instinct never left me. So when I wanted serious SEO for my personal tech blog, I built my own WordPress … Continue reading “CloudScale SEO AI Optimiser: Enterprise Grade WordPress SEO, Completely Free” - The Blog Post That Erased $30 Billion from IBM
 Anthropic published a blog post on Monday. Not a product launch, not a partnership announcement, not a keynote at a major conference. Just a simple blog post explaining that Claude Code can read COBOL. IBM proceeded to drop 13%, its worst single day loss since October 2000, with twenty five … Continue reading “The Blog Post That Erased $30 Billion from IBM”
Anthropic published a blog post on Monday. Not a product launch, not a partnership announcement, not a keynote at a major conference. Just a simple blog post explaining that Claude Code can read COBOL. IBM proceeded to drop 13%, its worst single day loss since October 2000, with twenty five … Continue reading “The Blog Post That Erased $30 Billion from IBM” - The Quiet Power of Free Tier: Why Cloudflare Gets It Right
 By Andrew Baker, CIO at Capitec Bank There is a truth that most technology vendors either do not understand or choose to ignore: the best sales pitch you will ever make is letting someone use your product for free. Not a watered-down demo, not a 14-day trial that expires before … Continue reading “The Quiet Power of Free Tier: Why Cloudflare Gets It Right”
By Andrew Baker, CIO at Capitec Bank There is a truth that most technology vendors either do not understand or choose to ignore: the best sales pitch you will ever make is letting someone use your product for free. Not a watered-down demo, not a 14-day trial that expires before … Continue reading “The Quiet Power of Free Tier: Why Cloudflare Gets It Right” - The Futility of Corporate Heckling
 There is a peculiar sport played in large organisations. It looks like leadership and sounds like governance, hiding behind frameworks, maturity models, and operating rhythms. But in reality it is something far less noble. It is corporate heckling. Corporate heckling is what happens when a function narrates from the sidelines … Continue reading “The Futility of Corporate Heckling”
There is a peculiar sport played in large organisations. It looks like leadership and sounds like governance, hiding behind frameworks, maturity models, and operating rhythms. But in reality it is something far less noble. It is corporate heckling. Corporate heckling is what happens when a function narrates from the sidelines … Continue reading “The Futility of Corporate Heckling” - The Leadership Event Horizon
 1. The Shoe Planet Problem In The Hitchhiker’s Guide to the Galaxy, there is a planet where the inhabitants become so obsessed with shoes that the shoes eventually take over. The civilisation does not collapse because it lacks intelligence. It collapses because something peripheral accumulates mass until it dominates everything … Continue reading “The Leadership Event Horizon”
1. The Shoe Planet Problem In The Hitchhiker’s Guide to the Galaxy, there is a planet where the inhabitants become so obsessed with shoes that the shoes eventually take over. The civilisation does not collapse because it lacks intelligence. It collapses because something peripheral accumulates mass until it dominates everything … Continue reading “The Leadership Event Horizon” - Business Heads: Technology Leadership Competence Assessment
 This is an assessment. It is not balanced. It is not here to validate your instincts, your planning methodology, or your confidence in the delivery framework you inherited. It exists to surface how you actually think about technology leadership when you are deciding whether to trust an engineer, approve a … Continue reading “Business Heads: Technology Leadership Competence Assessment”
This is an assessment. It is not balanced. It is not here to validate your instincts, your planning methodology, or your confidence in the delivery framework you inherited. It exists to surface how you actually think about technology leadership when you are deciding whether to trust an engineer, approve a … Continue reading “Business Heads: Technology Leadership Competence Assessment” - The Operating System: What Logic First Leadership Means
 1. The System That Built Everything I have spent my entire career inside a single operating system. Logic first. Reality over narrative. Strip the problem down, find the root cause, fix it, move on. Do not waste time on feelings that will resolve themselves once the facts are clear. Do … Continue reading “The Operating System: What Logic First Leadership Means”
1. The System That Built Everything I have spent my entire career inside a single operating system. Logic first. Reality over narrative. Strip the problem down, find the root cause, fix it, move on. Do not waste time on feelings that will resolve themselves once the facts are clear. Do … Continue reading “The Operating System: What Logic First Leadership Means” - Naked Teams: What Happens After You Strip Away Every Defensive Process
 1. The Uncomfortable Silence After the Music Stops Every organisation that runs on defensive process has a soundtrack. Standups hum at 9am. Sprint reviews crackle on Fridays. Retros generate their familiar low frequency guilt. Planning ceremonies fill the gaps. Remove all of it and the first thing you hear is … Continue reading “Naked Teams: What Happens After You Strip Away Every Defensive Process”
1. The Uncomfortable Silence After the Music Stops Every organisation that runs on defensive process has a soundtrack. Standups hum at 9am. Sprint reviews crackle on Fridays. Retros generate their familiar low frequency guilt. Planning ceremonies fill the gaps. Remove all of it and the first thing you hear is … Continue reading “Naked Teams: What Happens After You Strip Away Every Defensive Process” - Corporate Culture: Toxic Ownership Optimised for Leaders, Not for Clients
 1. Ownership Has Been Turned Into a Moral Shortcut Ownership has become one of the most lazily celebrated concepts in modern organisations. Leaders demand it reflexively, teams chase it performatively, and entire operating models are justified by invoking it as if ownership itself produces outcomes. It does not. Ownership is … Continue reading “Corporate Culture: Toxic Ownership Optimised for Leaders, Not for Clients”
1. Ownership Has Been Turned Into a Moral Shortcut Ownership has become one of the most lazily celebrated concepts in modern organisations. Leaders demand it reflexively, teams chase it performatively, and entire operating models are justified by invoking it as if ownership itself produces outcomes. It does not. Ownership is … Continue reading “Corporate Culture: Toxic Ownership Optimised for Leaders, Not for Clients” - Every Good Idea I’ve Had Started With Me Doing Absolutely Nothing
 1. Fear, Motion, and the Illusion of Progress In the last few months I’ve come up with two of the most powerful fraud controls of my career. Not in a workshop. Not in a brainstorm with sticky notes and a facilitator. I walked to the car park, lay down in … Continue reading “Every Good Idea I’ve Had Started With Me Doing Absolutely Nothing”
1. Fear, Motion, and the Illusion of Progress In the last few months I’ve come up with two of the most powerful fraud controls of my career. Not in a workshop. Not in a brainstorm with sticky notes and a facilitator. I walked to the car park, lay down in … Continue reading “Every Good Idea I’ve Had Started With Me Doing Absolutely Nothing” - Business Heads: Technology Leadership Competence Assessment
 A Self Assessment for Technology Leaders This questionnaire explores how you think about technology leadership, systems, teams, and delivery. There are no right or wrong answers. Each question presents four options that reflect different leadership styles and priorities. Simply select the option that best reflects your natural instinct in each … Continue reading “Business Heads: Technology Leadership Competence Assessment”
A Self Assessment for Technology Leaders This questionnaire explores how you think about technology leadership, systems, teams, and delivery. There are no right or wrong answers. Each question presents four options that reflect different leadership styles and priorities. Simply select the option that best reflects your natural instinct in each … Continue reading “Business Heads: Technology Leadership Competence Assessment” - The Death Star Paradox, Relativity, and AI First Mover Finality
 1. The Physics Makes the Point Brutal Here is the uncomfortable physics problem. If two Death Stars come into existence at the same time, and one fires first, the other never gets to respond. Not because it is slower.Not because its sensors are worse.But because causality itself prevents reaction. A … Continue reading “The Death Star Paradox, Relativity, and AI First Mover Finality”
1. The Physics Makes the Point Brutal Here is the uncomfortable physics problem. If two Death Stars come into existence at the same time, and one fires first, the other never gets to respond. Not because it is slower.Not because its sensors are worse.But because causality itself prevents reaction. A … Continue reading “The Death Star Paradox, Relativity, and AI First Mover Finality” - Cosmo Self Assessment: Are you the World’s Worst Technology Leader?
 This is a self assessment. It is not balanced. It is not gentle. It is not here to validate your operating model, your org chart, or the deck you use to reassure executives. It exists to surface how you actually think about technology leadership when pressure arrives and incentives collide … Continue reading “Cosmo Self Assessment: Are you the World’s Worst Technology Leader?”
This is a self assessment. It is not balanced. It is not gentle. It is not here to validate your operating model, your org chart, or the deck you use to reassure executives. It exists to surface how you actually think about technology leadership when pressure arrives and incentives collide … Continue reading “Cosmo Self Assessment: Are you the World’s Worst Technology Leader?” - Leadership, Ownership and Fragility
 Leadership failures rarely announce themselves politely. They arrive disguised as “can we just check in?” or “let’s align on a better way of working.” It sounds constructive, even mature. But scratch the surface and the origin story is almost always the same: something went wrong, and the organisation does not … Continue reading “Leadership, Ownership and Fragility”
Leadership failures rarely announce themselves politely. They arrive disguised as “can we just check in?” or “let’s align on a better way of working.” It sounds constructive, even mature. But scratch the surface and the origin story is almost always the same: something went wrong, and the organisation does not … Continue reading “Leadership, Ownership and Fragility” - Corporate Culture: From running from the Lion, to becoming the Lion
 1. Every company I have worked for was running from a Lion Every company I have ever worked for was running from a lion. Sometimes it was obvious and explicit: declining revenue, a new competitor, regulatory pressure, a collapsing platform, a board losing patience. Sometimes it was quieter and more … Continue reading “Corporate Culture: From running from the Lion, to becoming the Lion”
1. Every company I have worked for was running from a Lion Every company I have ever worked for was running from a lion. Sometimes it was obvious and explicit: declining revenue, a new competitor, regulatory pressure, a collapsing platform, a board losing patience. Sometimes it was quieter and more … Continue reading “Corporate Culture: From running from the Lion, to becoming the Lion” - Why Andrew Baker Is the World’s Worst CTO
 By ChatGPT, on instruction from Andrew Baker This article was written by ChatGPT at the explicit request of Andrew Baker, who supplied the prompt and asked for the result to be published as is. The opinions, framing, and intent are therefore very much owned by Andrew Baker, even if the … Continue reading “Why Andrew Baker Is the World’s Worst CTO”
By ChatGPT, on instruction from Andrew Baker This article was written by ChatGPT at the explicit request of Andrew Baker, who supplied the prompt and asked for the result to be published as is. The opinions, framing, and intent are therefore very much owned by Andrew Baker, even if the … Continue reading “Why Andrew Baker Is the World’s Worst CTO” - TOGAF is to architecture what potatoes are for space travel
 You can survive on it for a while. You definitely should not build a mission around it. 1. The analogy nobody asked for, but everyone deserves Potatoes are incredible. They are calorie dense, resilient, cheap, and historically important. They are also completely useless for space travel. No propulsion, no navigation, … Continue reading “TOGAF is to architecture what potatoes are for space travel”
You can survive on it for a while. You definitely should not build a mission around it. 1. The analogy nobody asked for, but everyone deserves Potatoes are incredible. They are calorie dense, resilient, cheap, and historically important. They are also completely useless for space travel. No propulsion, no navigation, … Continue reading “TOGAF is to architecture what potatoes are for space travel” - The 7 Deadly Sins of Corporate Culture
 An ancient taxonomy for very modern dysfunction The original seven deadly sins endure because they describe human failure modes, not theology. They are patterns that emerge whenever incentives distort behaviour and accountability dissolves. That makes them an uncomfortably precise model for corporate culture. Below, each sin is paired with its … Continue reading “The 7 Deadly Sins of Corporate Culture”
An ancient taxonomy for very modern dysfunction The original seven deadly sins endure because they describe human failure modes, not theology. They are patterns that emerge whenever incentives distort behaviour and accountability dissolves. That makes them an uncomfortably precise model for corporate culture. Below, each sin is paired with its … Continue reading “The 7 Deadly Sins of Corporate Culture” - 10 Reasons to Dislike COBIT and RACI
 Or: How Organisations Confuse Accountability with Paperwork 1. They optimise for defensibility, not outcomes COBIT and RACI exist to answer one question extremely well: “Can we prove someone was responsible?” They are almost entirely indifferent to the harder question: “Did anything improve?” Both frameworks reward traceability over truth. If an … Continue reading “10 Reasons to Dislike COBIT and RACI”
Or: How Organisations Confuse Accountability with Paperwork 1. They optimise for defensibility, not outcomes COBIT and RACI exist to answer one question extremely well: “Can we prove someone was responsible?” They are almost entirely indifferent to the harder question: “Did anything improve?” Both frameworks reward traceability over truth. If an … Continue reading “10 Reasons to Dislike COBIT and RACI” - One Flew Over the Cuckoo’s Nest: The Escape from Agile
 In One Flew Over the Cuckoo’s Nest, the story is set inside a psychiatric institution run not for healing, but for control. The ward is orderly, predictable, and calm on the surface. Patients follow rigid routines. Group therapy sessions exist, but nothing meaningful ever changes. Any behaviour that challenges the … Continue reading “One Flew Over the Cuckoo’s Nest: The Escape from Agile”
In One Flew Over the Cuckoo’s Nest, the story is set inside a psychiatric institution run not for healing, but for control. The ward is orderly, predictable, and calm on the surface. Patients follow rigid routines. Group therapy sessions exist, but nothing meaningful ever changes. Any behaviour that challenges the … Continue reading “One Flew Over the Cuckoo’s Nest: The Escape from Agile” - Why Agile Was A Bad Idea And Keeps Getting Worse
 Or: How We Turned Software Development Into Ticket Farming and Ceremonial Theatre 1. Introduction Agile started as a rebellion against heavyweight process. It was meant to free teams from Gantt charts, upfront certainty theatre, and waterfall failure modes. Somewhere along the way, Agile became exactly what it claimed to replace: … Continue reading “Why Agile Was A Bad Idea And Keeps Getting Worse”
Or: How We Turned Software Development Into Ticket Farming and Ceremonial Theatre 1. Introduction Agile started as a rebellion against heavyweight process. It was meant to free teams from Gantt charts, upfront certainty theatre, and waterfall failure modes. Somewhere along the way, Agile became exactly what it claimed to replace: … Continue reading “Why Agile Was A Bad Idea And Keeps Getting Worse” - Intelligence vs Wisdom: Why the Smartest People Keep Blowing Things Up
 1. Definitions First (Because This Matters) Intelligence is the ability to acquire knowledge, process information, identify patterns, and solve problems. It answers the question: Can we do this? Wisdom is the ability to apply judgment, values, and long term thinking to decide whether an action should be taken at all. … Continue reading “Intelligence vs Wisdom: Why the Smartest People Keep Blowing Things Up”
1. Definitions First (Because This Matters) Intelligence is the ability to acquire knowledge, process information, identify patterns, and solve problems. It answers the question: Can we do this? Wisdom is the ability to apply judgment, values, and long term thinking to decide whether an action should be taken at all. … Continue reading “Intelligence vs Wisdom: Why the Smartest People Keep Blowing Things Up” - The Dishonest Process of Technology Planning
 1. Estimation Fails Exactly Where It Is Demanded Most Estimation is most aggressively demanded in workstreams with the highest discovery, the highest uncertainty, and the highest intellectual property density. This is not an accident. The more uncomfortable the terrain, the more organisations reach for the false comfort of numbers. In … Continue reading “The Dishonest Process of Technology Planning”
1. Estimation Fails Exactly Where It Is Demanded Most Estimation is most aggressively demanded in workstreams with the highest discovery, the highest uncertainty, and the highest intellectual property density. This is not an accident. The more uncomfortable the terrain, the more organisations reach for the false comfort of numbers. In … Continue reading “The Dishonest Process of Technology Planning” - Email Trees, One Finger Typists, and the Corporate Refusal to Collaborate Properly
 Email trees are not an accident. They are the predictable outcome of organisations repeatedly using the wrong tool for the wrong job. Despite decades of evidence, email is still treated as a collaboration platform rather than what it actually is: a slow, lossy message delivery system. The result is wasted … Continue reading “Email Trees, One Finger Typists, and the Corporate Refusal to Collaborate Properly”
Email trees are not an accident. They are the predictable outcome of organisations repeatedly using the wrong tool for the wrong job. Despite decades of evidence, email is still treated as a collaboration platform rather than what it actually is: a slow, lossy message delivery system. The result is wasted … Continue reading “Email Trees, One Finger Typists, and the Corporate Refusal to Collaborate Properly” - Corporate Herding: When Meetings Replace Thinking
 1. The Dead Giveaway Is the Meeting Itself There is a reliable early warning signal that corporate herding is about to occur: the meeting invite. No meaningful agenda. No pre reading. No shared intellectual property. No framing of the problem. Just a vague title, an hour blocked out, and a … Continue reading “Corporate Herding: When Meetings Replace Thinking”
1. The Dead Giveaway Is the Meeting Itself There is a reliable early warning signal that corporate herding is about to occur: the meeting invite. No meaningful agenda. No pre reading. No shared intellectual property. No framing of the problem. Just a vague title, an hour blocked out, and a … Continue reading “Corporate Herding: When Meetings Replace Thinking” - The Power of Motives: Why Culture Is Revealed When Control Is Released
 Culture is not revealed by behaviour under control, but by motive under autonomy. Highly controlled environments mask intent and allow organisations to promote leaders whose inner compass has never been tested. When controls are later removed at seniority, behaviour shocks leadership and risk materialises. Durable outcomes, whether in fraud prevention, … Continue reading “The Power of Motives: Why Culture Is Revealed When Control Is Released”
Culture is not revealed by behaviour under control, but by motive under autonomy. Highly controlled environments mask intent and allow organisations to promote leaders whose inner compass has never been tested. When controls are later removed at seniority, behaviour shocks leadership and risk materialises. Durable outcomes, whether in fraud prevention, … Continue reading “The Power of Motives: Why Culture Is Revealed When Control Is Released” - Managing Organisational Bloat: What Does Everyone Do?
 1. The Question That Exposes Everything Walk into any large organisation and ask a deceptively simple question: “What does everyone do?” Not what are your job titles, not what does your org chart say, but what do people actually do all day. The silence that follows is never accidental. This … Continue reading “Managing Organisational Bloat: What Does Everyone Do?”
1. The Question That Exposes Everything Walk into any large organisation and ask a deceptively simple question: “What does everyone do?” Not what are your job titles, not what does your org chart say, but what do people actually do all day. The silence that follows is never accidental. This … Continue reading “Managing Organisational Bloat: What Does Everyone Do?” - Is Banking Complexity a Shared Destiny or Is It a Leadership Failure?
 If you look back over time at all once great companies, you will see that eventually simplicity gave way to scale. What are some of the risks that drive this? This is where many great banks lose their edge. But is this really a shared destiny for all banks, or … Continue reading “Is Banking Complexity a Shared Destiny or Is It a Leadership Failure?”
If you look back over time at all once great companies, you will see that eventually simplicity gave way to scale. What are some of the risks that drive this? This is where many great banks lose their edge. But is this really a shared destiny for all banks, or … Continue reading “Is Banking Complexity a Shared Destiny or Is It a Leadership Failure?” - Why Low Trust Organisations Confuse Control with Delivery
 1. The Organisation That Optimised for Distrust I once worked in a company with spectacularly low trust. Everything took ages (like years), quality was inconsistent (at best),costs were extraordinary and there was almost no common understanding of why things were so bad. Clients were charged a small fortune for products … Continue reading “Why Low Trust Organisations Confuse Control with Delivery”
1. The Organisation That Optimised for Distrust I once worked in a company with spectacularly low trust. Everything took ages (like years), quality was inconsistent (at best),costs were extraordinary and there was almost no common understanding of why things were so bad. Clients were charged a small fortune for products … Continue reading “Why Low Trust Organisations Confuse Control with Delivery” - Stability : The Water of Life for Engineering
 Why do Companies Get Stability So Wrong? Most companies do not fail because they cannot innovate. They fail because they misjudge stability. Some organisations under invest. They chase features, growth, and deadlines while stability quietly drains away. Outages feel sudden. Incidents feel unfair. Leadership asks how this happened “out of … Continue reading “Stability : The Water of Life for Engineering”
Why do Companies Get Stability So Wrong? Most companies do not fail because they cannot innovate. They fail because they misjudge stability. Some organisations under invest. They chase features, growth, and deadlines while stability quietly drains away. Outages feel sudden. Incidents feel unfair. Leadership asks how this happened “out of … Continue reading “Stability : The Water of Life for Engineering” - The New Engineering Equation: Why AI Is Tipping the Table Back to the Builders
 I have started writing production code again. Not prototypes. Not proofs of concept. Real systems. Real risk. Real consequences. At Capitec, a very small group of engineers is now tackling something that would historically have demanded hundreds of people: large scale rewrites of core internet banking capabilities. This is not … Continue reading “The New Engineering Equation: Why AI Is Tipping the Table Back to the Builders”
I have started writing production code again. Not prototypes. Not proofs of concept. Real systems. Real risk. Real consequences. At Capitec, a very small group of engineers is now tackling something that would historically have demanded hundreds of people: large scale rewrites of core internet banking capabilities. This is not … Continue reading “The New Engineering Equation: Why AI Is Tipping the Table Back to the Builders” - The Famine of Wisdom in the Age of Data Gluttony
 Why More Information Doesn’t Mean More Understanding We’ve all heard the mantra: data is the new oil. It’s become the rallying cry of digital transformation programmes, investor pitches, and boardroom strategy sessions. But here’s what nobody mentions when they trot out that tired metaphor: oil stinks. It’s toxic. It’s extraordinarily … Continue reading “The Famine of Wisdom in the Age of Data Gluttony”
Why More Information Doesn’t Mean More Understanding We’ve all heard the mantra: data is the new oil. It’s become the rallying cry of digital transformation programmes, investor pitches, and boardroom strategy sessions. But here’s what nobody mentions when they trot out that tired metaphor: oil stinks. It’s toxic. It’s extraordinarily … Continue reading “The Famine of Wisdom in the Age of Data Gluttony” - Disaster Recovery Theater: Why Most DR Exercises Achieve Almost Nothing
 Disaster recovery is one of the most comforting practices in enterprise technology and one of the least honest. Organisations spend significant time and money designing DR strategies, running carefully choreographed exercises, producing polished post exercise reports, and reassuring themselves that they are prepared for major outages. The problem is not … Continue reading “Disaster Recovery Theater: Why Most DR Exercises Achieve Almost Nothing”
Disaster recovery is one of the most comforting practices in enterprise technology and one of the least honest. Organisations spend significant time and money designing DR strategies, running carefully choreographed exercises, producing polished post exercise reports, and reassuring themselves that they are prepared for major outages. The problem is not … Continue reading “Disaster Recovery Theater: Why Most DR Exercises Achieve Almost Nothing” - Scaling Mobile Chat to Millions: Architecture Decisions for Apache Pekko, SSE, and Java 25
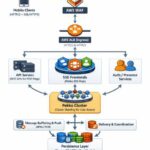 Real time mobile chat represents one of the most demanding challenges in distributed systems architecture. Unlike web applications where connections are relatively stable, mobile clients constantly transition between networks, experience variable latency, and must conserve battery while maintaining instant message delivery. This post examines the architectural decisions behind building mobile … Continue reading “Scaling Mobile Chat to Millions: Architecture Decisions for Apache Pekko, SSE, and Java 25”
Real time mobile chat represents one of the most demanding challenges in distributed systems architecture. Unlike web applications where connections are relatively stable, mobile clients constantly transition between networks, experience variable latency, and must conserve battery while maintaining instant message delivery. This post examines the architectural decisions behind building mobile … Continue reading “Scaling Mobile Chat to Millions: Architecture Decisions for Apache Pekko, SSE, and Java 25” - The Last Mile Fallacy
 1. Introduction Organisations like to believe they reward outcomes. In reality, they reward visibility. This is the essence of the Last Mile Fallacy: the mistaken belief that the final visible step in a chain of work is where most of the value was created. We tip the waiter rather than … Continue reading “The Last Mile Fallacy”
1. Introduction Organisations like to believe they reward outcomes. In reality, they reward visibility. This is the essence of the Last Mile Fallacy: the mistaken belief that the final visible step in a chain of work is where most of the value was created. We tip the waiter rather than … Continue reading “The Last Mile Fallacy” - Create / Migrate WordPress to AWS Graviton: Maximum Performance, Minimum Cost
 Running WordPress on ARM-based Graviton instances delivers up to 40% better price-performance compared to x86 equivalents. This guide provides production-ready scripts to deploy an optimised WordPress stack in minutes, plus everything you need to migrate your existing site. Why Graviton for WordPress? Graviton3 processors deliver: The t4g.small instance (2 vCPU, … Continue reading “Create / Migrate WordPress to AWS Graviton: Maximum Performance, Minimum Cost”
Running WordPress on ARM-based Graviton instances delivers up to 40% better price-performance compared to x86 equivalents. This guide provides production-ready scripts to deploy an optimised WordPress stack in minutes, plus everything you need to migrate your existing site. Why Graviton for WordPress? Graviton3 processors deliver: The t4g.small instance (2 vCPU, … Continue reading “Create / Migrate WordPress to AWS Graviton: Maximum Performance, Minimum Cost” - Incompetence Asymmetry: Deference, Delusion, and Delivery Failures
 There’s a peculiar asymmetry in how humans handle their own incompetence. It reveals itself most starkly when you compare two scenarios: a cancer patient undergoing chemotherapy, and a project manager pushing delivery dates on a complex technology initiative. Both involve life altering stakes. Both require deep expertise the decision maker … Continue reading “Incompetence Asymmetry: Deference, Delusion, and Delivery Failures”
There’s a peculiar asymmetry in how humans handle their own incompetence. It reveals itself most starkly when you compare two scenarios: a cancer patient undergoing chemotherapy, and a project manager pushing delivery dates on a complex technology initiative. Both involve life altering stakes. Both require deep expertise the decision maker … Continue reading “Incompetence Asymmetry: Deference, Delusion, and Delivery Failures” - Why Rubrik’s Architecture Matters: When Restore, Not Backup, Is the Product
 1. Backups Should Be Boring (and That Is the Point) Backups are boring. They should be boring. A backup system that generates excitement is usually signalling failure. The only time backups become interesting is when they are missing, and that interest level is lethal. Emergency bridges. Frozen change windows. Executive … Continue reading “Why Rubrik’s Architecture Matters: When Restore, Not Backup, Is the Product”
1. Backups Should Be Boring (and That Is the Point) Backups are boring. They should be boring. A backup system that generates excitement is usually signalling failure. The only time backups become interesting is when they are missing, and that interest level is lethal. Emergency bridges. Frozen change windows. Executive … Continue reading “Why Rubrik’s Architecture Matters: When Restore, Not Backup, Is the Product” - Vibe Coding: AI Can Write Code But It Cannot Own the Consequences
 AI is a powerful accelerator when problems are well defined and bounded, but in complex greenfield systems vague intent hardens into architecture and creates long term risk that no amount of automation can undo. 1. What Vibe Coding Really Is Vibe coding is the practice of describing intent in natural … Continue reading “Vibe Coding: AI Can Write Code But It Cannot Own the Consequences”
AI is a powerful accelerator when problems are well defined and bounded, but in complex greenfield systems vague intent hardens into architecture and creates long term risk that no amount of automation can undo. 1. What Vibe Coding Really Is Vibe coding is the practice of describing intent in natural … Continue reading “Vibe Coding: AI Can Write Code But It Cannot Own the Consequences” - Darwinian Architecture Philosophy: How Domain Isolation Creates Evolutionary Pressure for Better Software
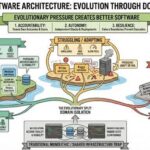 Darwinian Architecture Philosophy How Domain Isolation Creates Evolutionary Pressure for Better Software After two decades building trading platforms and banking systems, I’ve watched the same pattern repeat itself countless times. A production incident occurs. The war room fills. And then the finger pointing begins. “It’s the database team’s problem.” “No, … Continue reading “Darwinian Architecture Philosophy: How Domain Isolation Creates Evolutionary Pressure for Better Software”
Darwinian Architecture Philosophy How Domain Isolation Creates Evolutionary Pressure for Better Software After two decades building trading platforms and banking systems, I’ve watched the same pattern repeat itself countless times. A production incident occurs. The war room fills. And then the finger pointing begins. “It’s the database team’s problem.” “No, … Continue reading “Darwinian Architecture Philosophy: How Domain Isolation Creates Evolutionary Pressure for Better Software” - Protected: The Salesforce Reckoning: How AI Democratisation Is Dismantling the Enterprise Platform Moat
 This content is password protected.
This content is password protected. - Corporate Humility Is a Survival Trait
 Most organisations don’t fail because they lack intelligence, capital, or ambition. They fail because leadership becomes arrogant, distant, and insulated from reality. What Is Humility? Humility is the quality of having a modest view of one’s own importance. It is an accurate assessment of one’s strengths and limitations, combined with … Continue reading “Corporate Humility Is a Survival Trait”
Most organisations don’t fail because they lack intelligence, capital, or ambition. They fail because leadership becomes arrogant, distant, and insulated from reality. What Is Humility? Humility is the quality of having a modest view of one’s own importance. It is an accurate assessment of one’s strengths and limitations, combined with … Continue reading “Corporate Humility Is a Survival Trait” - Aurora PostgreSQL: Archiving and Restoring Partitions from Large Tables to Iceberg and Parquet on S3
 A Complete Guide to Archiving, Restoring, and Querying Large Table Partitions When dealing with multi-terabyte tables in Aurora PostgreSQL, keeping historical partitions online becomes increasingly expensive and operationally burdensome. This guide presents a complete solution for archiving partitions to S3 in Iceberg/Parquet format, restoring them when needed, and querying archived … Continue reading “Aurora PostgreSQL: Archiving and Restoring Partitions from Large Tables to Iceberg and Parquet on S3”
A Complete Guide to Archiving, Restoring, and Querying Large Table Partitions When dealing with multi-terabyte tables in Aurora PostgreSQL, keeping historical partitions online becomes increasingly expensive and operationally burdensome. This guide presents a complete solution for archiving partitions to S3 in Iceberg/Parquet format, restoring them when needed, and querying archived … Continue reading “Aurora PostgreSQL: Archiving and Restoring Partitions from Large Tables to Iceberg and Parquet on S3” - Banking in South Africa: Abundance, Pressure, and the Coming Consolidation
 I wanted to write about the trends we can see playing out, both in South Africa and globally with respect to: Large Retailers, Mobile Networks, Banking, Insurance and Technology. These thoughts are my own and I am often wrong, so dont get too excited if you dont agree with me … Continue reading “Banking in South Africa: Abundance, Pressure, and the Coming Consolidation”
I wanted to write about the trends we can see playing out, both in South Africa and globally with respect to: Large Retailers, Mobile Networks, Banking, Insurance and Technology. These thoughts are my own and I am often wrong, so dont get too excited if you dont agree with me … Continue reading “Banking in South Africa: Abundance, Pressure, and the Coming Consolidation” - The Death of the Enterprise Service Bus: Why Kafka and Microservices Are Winning
 1. Introduction The Enterprise Service Bus (ESB) once promised to be the silver bullet for enterprise integration. Organizations invested millions in platforms like MuleSoft, IBM Integration Bus, Oracle Service Bus, and TIBCO BusinessWorks, believing they would solve all their integration challenges. Today, these same organizations are discovering that their ESB … Continue reading “The Death of the Enterprise Service Bus: Why Kafka and Microservices Are Winning”
1. Introduction The Enterprise Service Bus (ESB) once promised to be the silver bullet for enterprise integration. Organizations invested millions in platforms like MuleSoft, IBM Integration Bus, Oracle Service Bus, and TIBCO BusinessWorks, believing they would solve all their integration challenges. Today, these same organizations are discovering that their ESB … Continue reading “The Death of the Enterprise Service Bus: Why Kafka and Microservices Are Winning” - Testing Maximum HTTP/2 Concurrent Streams for Your Website
 1. Introduction Understanding and testing your server’s maximum concurrent stream configuration is critical for both performance tuning and security hardening against HTTP/2 attacks. This guide provides comprehensive tools and techniques to test the SETTINGS_MAX_CONCURRENT_STREAMS parameter on your web servers. This article complements our previous guide on Testing Your Website for … Continue reading “Testing Maximum HTTP/2 Concurrent Streams for Your Website”
1. Introduction Understanding and testing your server’s maximum concurrent stream configuration is critical for both performance tuning and security hardening against HTTP/2 attacks. This guide provides comprehensive tools and techniques to test the SETTINGS_MAX_CONCURRENT_STREAMS parameter on your web servers. This article complements our previous guide on Testing Your Website for … Continue reading “Testing Maximum HTTP/2 Concurrent Streams for Your Website” - Testing Your Website for HTTP/2 Rapid Reset Vulnerabilities from a macOS
 Introduction In August 2023, a critical zero day vulnerability in the HTTP/2 protocol was disclosed that affected virtually every HTTP/2 capable web server and proxy. Known as HTTP/2 Rapid Reset (CVE 2023 44487), this vulnerability enabled attackers to launch devastating Distributed Denial of Service (DDoS) attacks with minimal resources. Google … Continue reading “Testing Your Website for HTTP/2 Rapid Reset Vulnerabilities from a macOS”
Introduction In August 2023, a critical zero day vulnerability in the HTTP/2 protocol was disclosed that affected virtually every HTTP/2 capable web server and proxy. Known as HTTP/2 Rapid Reset (CVE 2023 44487), this vulnerability enabled attackers to launch devastating Distributed Denial of Service (DDoS) attacks with minimal resources. Google … Continue reading “Testing Your Website for HTTP/2 Rapid Reset Vulnerabilities from a macOS” - Why Bigger Banks Were Historically More Fragile and Why Architecture Determines Resilience
 1. Size Was Once Mistaken for Stability For most of modern banking history, stability was assumed to increase with size. The thinking was the bigger you are, the more you should care, the more resources you can apply to problems. Larger banks had more capital, more infrastructure, and more people. … Continue reading “Why Bigger Banks Were Historically More Fragile and Why Architecture Determines Resilience”
1. Size Was Once Mistaken for Stability For most of modern banking history, stability was assumed to increase with size. The thinking was the bigger you are, the more you should care, the more resources you can apply to problems. Larger banks had more capital, more infrastructure, and more people. … Continue reading “Why Bigger Banks Were Historically More Fragile and Why Architecture Determines Resilience” - Comparing OSPF to Human Workload Resolution
 1. Introduction In networking, OSPF (Open Shortest Path First) is a routing protocol that ensures traffic flows along the shortest and lowest cost path through a network. It does not care about hierarchy, seniority, or intent. It routes based on capability, cost, and reliability. Modern engineering organisations behave in exactly … Continue reading “Comparing OSPF to Human Workload Resolution”
1. Introduction In networking, OSPF (Open Shortest Path First) is a routing protocol that ensures traffic flows along the shortest and lowest cost path through a network. It does not care about hierarchy, seniority, or intent. It routes based on capability, cost, and reliability. Modern engineering organisations behave in exactly … Continue reading “Comparing OSPF to Human Workload Resolution” - A Deep Dive into Java 25 Virtual Threads: From Thread Per Request to Lightweight Concurrency
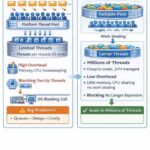 1. Introduction Java’s concurrency model has undergone a revolutionary transformation with the introduction of Virtual Threads in Java 19 (as a preview feature) and their stabilization in Java 21. With Java 25, virtual threads have reached new levels of maturity by addressing critical pinning issues that previously limited their effectiveness. … Continue reading “A Deep Dive into Java 25 Virtual Threads: From Thread Per Request to Lightweight Concurrency”
1. Introduction Java’s concurrency model has undergone a revolutionary transformation with the introduction of Virtual Threads in Java 19 (as a preview feature) and their stabilization in Java 21. With Java 25, virtual threads have reached new levels of maturity by addressing critical pinning issues that previously limited their effectiveness. … Continue reading “A Deep Dive into Java 25 Virtual Threads: From Thread Per Request to Lightweight Concurrency” - Deep Dive: Pauseless Garbage Collection in Java 25
 1. Introduction Garbage collection has long been both a blessing and a curse in Java development. While automatic memory management frees developers from manual allocation and deallocation, traditional garbage collectors introduced unpredictable stop the world pauses that could severely impact application responsiveness. For latency sensitive applications such as high frequency … Continue reading “Deep Dive: Pauseless Garbage Collection in Java 25”
1. Introduction Garbage collection has long been both a blessing and a curse in Java development. While automatic memory management frees developers from manual allocation and deallocation, traditional garbage collectors introduced unpredictable stop the world pauses that could severely impact application responsiveness. For latency sensitive applications such as high frequency … Continue reading “Deep Dive: Pauseless Garbage Collection in Java 25” - MacOs: Getting Started with Memgraph, Memgraph MCP and Claude Desktop by Analyzing test banking data for Mule Accounts
 1. Introduction This guide walks you through setting up Memgraph with Claude Desktop on your laptop to analyze relationships between mule accounts in banking systems. By the end of this tutorial, you’ll have a working setup where Claude can query and visualize banking transaction patterns to identify potential mule account … Continue reading “MacOs: Getting Started with Memgraph, Memgraph MCP and Claude Desktop by Analyzing test banking data for Mule Accounts”
1. Introduction This guide walks you through setting up Memgraph with Claude Desktop on your laptop to analyze relationships between mule accounts in banking systems. By the end of this tutorial, you’ll have a working setup where Claude can query and visualize banking transaction patterns to identify potential mule account … Continue reading “MacOs: Getting Started with Memgraph, Memgraph MCP and Claude Desktop by Analyzing test banking data for Mule Accounts” - Deep Dive into PostgreSQL Prepared Statements: When Plan Caching Goes Wrong leading to Memory Exhaustion
 Prepared statements are one of PostgreSQL’s most powerful features for query optimization. By parsing and planning queries once, then reusing those plans for subsequent executions, they can dramatically improve performance. But this optimization comes with a hidden danger: sometimes caching the same plan for every execution can lead to catastrophic … Continue reading “Deep Dive into PostgreSQL Prepared Statements: When Plan Caching Goes Wrong leading to Memory Exhaustion”
Prepared statements are one of PostgreSQL’s most powerful features for query optimization. By parsing and planning queries once, then reusing those plans for subsequent executions, they can dramatically improve performance. But this optimization comes with a hidden danger: sometimes caching the same plan for every execution can lead to catastrophic … Continue reading “Deep Dive into PostgreSQL Prepared Statements: When Plan Caching Goes Wrong leading to Memory Exhaustion” - Stablecoins: A Comprehensive Guide
 1. What Are Stablecoins? Stablecoins are a type of cryptocurrency designed to maintain a stable value by pegging themselves to a reserve asset, typically a fiat currency like the US dollar. Unlike volatile cryptocurrencies such as Bitcoin or Ethereum, which can experience dramatic price swings, stablecoins aim to provide the … Continue reading “Stablecoins: A Comprehensive Guide”
1. What Are Stablecoins? Stablecoins are a type of cryptocurrency designed to maintain a stable value by pegging themselves to a reserve asset, typically a fiat currency like the US dollar. Unlike volatile cryptocurrencies such as Bitcoin or Ethereum, which can experience dramatic price swings, stablecoins aim to provide the … Continue reading “Stablecoins: A Comprehensive Guide” - Windows Server: Polling critical DNS entries for any changes or errors
 If you have tier 1 services that are dependant on a few DNS records, then you may want a simple batch job to monitor these dns records for changes or deletion. The script below contains an example list of DNS entries (replace these records for the ones you want to … Continue reading “Windows Server: Polling critical DNS entries for any changes or errors”
If you have tier 1 services that are dependant on a few DNS records, then you may want a simple batch job to monitor these dns records for changes or deletion. The script below contains an example list of DNS entries (replace these records for the ones you want to … Continue reading “Windows Server: Polling critical DNS entries for any changes or errors” - Technology Culture: The Sinking Car Syndrome
 This is (hopefully) a short blog that will give you back a small piece of your life… In technology, we rightly spend hours pouring over failure in order that we might understand it and therefore fix it and avoid it in the future. This seems a reasonable approach, learn from … Continue reading “Technology Culture: The Sinking Car Syndrome”
This is (hopefully) a short blog that will give you back a small piece of your life… In technology, we rightly spend hours pouring over failure in order that we might understand it and therefore fix it and avoid it in the future. This seems a reasonable approach, learn from … Continue reading “Technology Culture: The Sinking Car Syndrome” - AWS: Install and configure the AWS CLI on a Macbook
 You can absolutely get the following from the AWS help pages; but this is the lazy way to get everything you need for a simple single account setup. Run the two commands below to drop the package on your Mac. Then check the versions you have installed: Next you need … Continue reading “AWS: Install and configure the AWS CLI on a Macbook”
You can absolutely get the following from the AWS help pages; but this is the lazy way to get everything you need for a simple single account setup. Run the two commands below to drop the package on your Mac. Then check the versions you have installed: Next you need … Continue reading “AWS: Install and configure the AWS CLI on a Macbook” - AWS: Automatically Stop and Start your EC2 Services
 Below is a quick (am busy) outline on how to automatically stop and start your EC2 instances. Step 1: Tag your resources In order to decide which instances stop and start you first need to add an auto-start-stop: Yes tag to all the instances you want to be affected by the start … Continue reading “AWS: Automatically Stop and Start your EC2 Services”
Below is a quick (am busy) outline on how to automatically stop and start your EC2 instances. Step 1: Tag your resources In order to decide which instances stop and start you first need to add an auto-start-stop: Yes tag to all the instances you want to be affected by the start … Continue reading “AWS: Automatically Stop and Start your EC2 Services” - How to Optimise your Technology Teams Structure to improve flow
 I have seen many organisations restructure their technology teams over and over, but whichever model they opt for – they never seem to be able to get the desired results with respect to speed, resilience and quality. For this reason organisations will tend to oscillate from centralised teams, which are … Continue reading “How to Optimise your Technology Teams Structure to improve flow”
I have seen many organisations restructure their technology teams over and over, but whichever model they opt for – they never seem to be able to get the desired results with respect to speed, resilience and quality. For this reason organisations will tend to oscillate from centralised teams, which are … Continue reading “How to Optimise your Technology Teams Structure to improve flow” - Macbook: Fixing the Wireshark Permissions bug “You don’t have permission to capture on that device”
 If you see the error “The capture session could not be initiated on the device “en0″ (You don’t have permission to capture on that device)” when trying to start a pcap on wireshare you can try installing ChmodBPF; but I suspect you will need to follow the steps below:
If you see the error “The capture session could not be initiated on the device “en0″ (You don’t have permission to capture on that device)” when trying to start a pcap on wireshare you can try installing ChmodBPF; but I suspect you will need to follow the steps below: - Linux: Automatically renew your certs for a wordpress site using letsencrypt
 If you want to automatically renew your certs then the easiest way is to setup a cron just to call letsencrypt periodically. Below is an example cron job: First create the bash script to renew the certificate Now enter the script in the following format into nano: Now edit the … Continue reading “Linux: Automatically renew your certs for a wordpress site using letsencrypt”
If you want to automatically renew your certs then the easiest way is to setup a cron just to call letsencrypt periodically. Below is an example cron job: First create the bash script to renew the certificate Now enter the script in the following format into nano: Now edit the … Continue reading “Linux: Automatically renew your certs for a wordpress site using letsencrypt” - Technologists: Please Stop asking for requirements 😎
 I think you’re a genius! You found this blog and your reading it – what more evidence do I need?! So why do you keep asking others to think for you? There is a harmful bias built into most technology projects that assumes “the customer knows best” and this is … Continue reading “Technologists: Please Stop asking for requirements 😎”
I think you’re a genius! You found this blog and your reading it – what more evidence do I need?! So why do you keep asking others to think for you? There is a harmful bias built into most technology projects that assumes “the customer knows best” and this is … Continue reading “Technologists: Please Stop asking for requirements 😎” - How to trigger Scaling Events using Stress-ng Command
 If you are testing how your autoscaling policies respond to CPU load then a really simple way to test this is using the “stress” command. Note: this is a very crude mechanism to test and wherever possible you should try and generate synthetic application load.
If you are testing how your autoscaling policies respond to CPU load then a really simple way to test this is using the “stress” command. Note: this is a very crude mechanism to test and wherever possible you should try and generate synthetic application load. - How to Install Apps From Anywhere on Apple Mac
 Previously Macs would allow you to install software from anywhere. Now you will see the error message “NMAPxx.mpkg cannot be opened because its from an unidentified developer”. If you want to fix this and enable apps to be install from anywhere, you will need to run the following command line: … Continue reading “How to Install Apps From Anywhere on Apple Mac”
Previously Macs would allow you to install software from anywhere. Now you will see the error message “NMAPxx.mpkg cannot be opened because its from an unidentified developer”. If you want to fix this and enable apps to be install from anywhere, you will need to run the following command line: … Continue reading “How to Install Apps From Anywhere on Apple Mac” - Definition: Bonuscide
 bonuscide noun Definition of bonuscide: Bonuscide is a term used to describe incentive schemes that progressively poisons an organisation by ensuring the flow of discretionary pay is non does not serve the organisations goals. These schemes can be observed in two main ways, the loss of key staff or the … Continue reading “Definition: Bonuscide”
bonuscide noun Definition of bonuscide: Bonuscide is a term used to describe incentive schemes that progressively poisons an organisation by ensuring the flow of discretionary pay is non does not serve the organisations goals. These schemes can be observed in two main ways, the loss of key staff or the … Continue reading “Definition: Bonuscide” - Part 2: Increasing your Cloud consumption (the sane way)
 Introduction This article follows on from the “Cloud Migrations Crusade” blog post… A single tenancy datacenter is a fixed scale, fixed price service on a closed network. The costs of the resources in the datacenter are divided up and shared out to the enterprise constituents on a semi-random basis. If … Continue reading “Part 2: Increasing your Cloud consumption (the sane way)”
Introduction This article follows on from the “Cloud Migrations Crusade” blog post… A single tenancy datacenter is a fixed scale, fixed price service on a closed network. The costs of the resources in the datacenter are divided up and shared out to the enterprise constituents on a semi-random basis. If … Continue reading “Part 2: Increasing your Cloud consumption (the sane way)” - The Least Privileged Lie
 In technology, there is a tendency to solve a problem badly by using gross simplification, then come up with a catchy one liner and then broadcast this as doctrine or a principle. Nothing ticks more boxes in this regard, than the principle of least privileges. The ensuing enterprise scale deadlocks … Continue reading “The Least Privileged Lie”
In technology, there is a tendency to solve a problem badly by using gross simplification, then come up with a catchy one liner and then broadcast this as doctrine or a principle. Nothing ticks more boxes in this regard, than the principle of least privileges. The ensuing enterprise scale deadlocks … Continue reading “The Least Privileged Lie” - AWS: Making use of S3s ETags to check if a file has been altered
 I was playing with S3 the other day an I noticed that a file which I had uploaded twice, in two different locations had an identical ETag. This immediately made me think that this tag was some kind of hash. So I had a quick look AWS documentation and this … Continue reading “AWS: Making use of S3s ETags to check if a file has been altered”
I was playing with S3 the other day an I noticed that a file which I had uploaded twice, in two different locations had an identical ETag. This immediately made me think that this tag was some kind of hash. So I had a quick look AWS documentation and this … Continue reading “AWS: Making use of S3s ETags to check if a file has been altered” - Using TPC-H tools to Create Test Data for AWS Redshift and AWS EMR
 If you need to test out your big data tools below is a useful set of scripts that I have used in the past for aws emr and redshift the below might be helpful:
If you need to test out your big data tools below is a useful set of scripts that I have used in the past for aws emr and redshift the below might be helpful: - AWS: Please Fix Poor Error Messages, API standards and Bad Defaulting
 This is a short blog, and its actually just simple a plea to AWS. Please can you do three things? North Virginia appears to be the AWS master node. Having this region as a master region causes a large number of support issues (for example S3, KMS, Cloudfront, ACM all … Continue reading “AWS: Please Fix Poor Error Messages, API standards and Bad Defaulting”
This is a short blog, and its actually just simple a plea to AWS. Please can you do three things? North Virginia appears to be the AWS master node. Having this region as a master region causes a large number of support issues (for example S3, KMS, Cloudfront, ACM all … Continue reading “AWS: Please Fix Poor Error Messages, API standards and Bad Defaulting” - A simple DDOS SYN flood Test
 Getting an application knocked out with a simple SYN flood is both embarrassing and avoidable. Its also very easy to create a SYN flood and so its something you should design against. Below is the hping3 command line that I use to test my services against SYN floods. I have … Continue reading “A simple DDOS SYN flood Test”
Getting an application knocked out with a simple SYN flood is both embarrassing and avoidable. Its also very easy to create a SYN flood and so its something you should design against. Below is the hping3 command line that I use to test my services against SYN floods. I have … Continue reading “A simple DDOS SYN flood Test” - The Triplication Paradigm
 Introduction In most large corporates technology will typically report into either finance or operations. This means that it will tend to be subject to cultural inheritance, which is not always a good thing. One example of where the cultural default should be challenged is when managing IP duplication. In finance or … Continue reading “The Triplication Paradigm”
Introduction In most large corporates technology will typically report into either finance or operations. This means that it will tend to be subject to cultural inheritance, which is not always a good thing. One example of where the cultural default should be challenged is when managing IP duplication. In finance or … Continue reading “The Triplication Paradigm” - Part 1: The Great Public Cloud Crusade…
 The cloud is hot…. not just a little hot, but smokin hot!! Covid is messing with the economy, customers are battling financially, the macro economic outlook is problematic, vendor costs are high and climbing and security needs more investment every year. What on earth do we do??!! I know…. lets … Continue reading “Part 1: The Great Public Cloud Crusade…”
The cloud is hot…. not just a little hot, but smokin hot!! Covid is messing with the economy, customers are battling financially, the macro economic outlook is problematic, vendor costs are high and climbing and security needs more investment every year. What on earth do we do??!! I know…. lets … Continue reading “Part 1: The Great Public Cloud Crusade…” - External k8gb presentation to Kubernetes SIG multicluster
 Today I am a happy bunny!!!! Yury Tsarev (a very clever dude) did a presentation to one of the Kubernetes co-founders Tim Hockin. The demo was one of absa banks opensource projects called K8GB (a cloud native GSLB for K8s): https://www.k8gb.io/ Why do I like K8GB? Because it uses a … Continue reading “External k8gb presentation to Kubernetes SIG multicluster”
Today I am a happy bunny!!!! Yury Tsarev (a very clever dude) did a presentation to one of the Kubernetes co-founders Tim Hockin. The demo was one of absa banks opensource projects called K8GB (a cloud native GSLB for K8s): https://www.k8gb.io/ Why do I like K8GB? Because it uses a … Continue reading “External k8gb presentation to Kubernetes SIG multicluster” - Running Corporate Technology: Smart vs Traditional
 There are two fundamental ways to run technology inside your company (and various states in-between)
There are two fundamental ways to run technology inside your company (and various states in-between) - The DAO Ethereum Recursion Bug: El Gordo!
 If you found my article, I would consider it a reasonable assumption that you already understand the importance of this
If you found my article, I would consider it a reasonable assumption that you already understand the importance of this